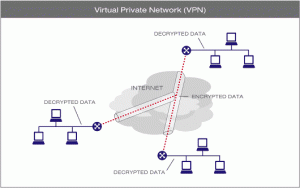
Purpose:
A Virtual Private Network (VPN) network provides secure access to online data by creating a private network with which to access both the public Internet and other internal organisational networks. A VPN uses tunneling protocols thus encrypted data at the sending end and decrypted at the receiving end.
VPNs allow for greater privacy because data packets are encrypted as the move across the Internet making it difficult to know the activities of users. Additionally, it allows users to access private networks that run within organisations such as universities and companies. These allow users to access content that would not be available otherwise.
Techniques include, each have their own technical strengths and weaknesses [BPN01]:
- Layer 2 Tunnel Protocol (L2TP and L2TP/IPsec)
- Secure Socket Tunneling Protocol (SSTP)
- Internet Key Exchange (version 2) (IKEv2)
- OpenVPN
Capabilities:
- Tunneling – Creates a secure connect for data at both the sending and receiving ends of a network.
- Encryption – Data is packaged into secure envelopes, providing protection from packet sniffing [SCO01].
- IP cloaking – Masks the users originated IP address and allows people to appear as if they are accessing the Internet from another country or organisation.
Surveillance mitigation:
- Privacy – A secure and anonymous way to access content or conduct activities (e.g. online banking) on the Internet.
Vulnerabilities:
- VPN provider – The customer should ensure that their VPN service provider does not keep logs
- Decryption – Spiegel [SPI01] has reported that the NSA has a number of programmes that aim to compromise VPN security.
Layers of operation:
Sources:
Best VPN (BPN)
1) https://www.bestvpn.com/blog/4147/pptp-vs-l2tp-vs-openvpn-vs-sstp-vs-ikev2/
Spiegel (SPI)
1) http://www.spiegel.de/international/world/nsa-documents-attacks-on-vpn-ssl-tls-ssh-tor-a-1010525.html
Scott, C., Wolfe, P., Erwin, M (SCO), Virtual Private Networks. O’Reilly, 1999.
1) http://shop.oreilly.com/product/9781565925298.do